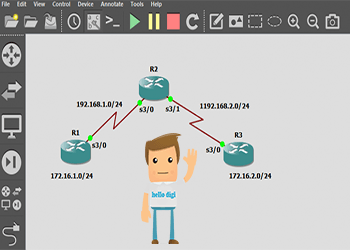
R3(config)#no sh
R3(config)#ip add 192.168.2.1 255.255.255.0
R3(config)#
R3(config)#ip route 192.168.1.0 255.255.255.0 s3/0
R3(config)#int tunnel 100
*Nov 11 17:28:21.051:
R3(config-if)#tunnel source s3/0
R3(config-if)#tunnel destination 192.168.1.1
*Nov 11 17:28:50.767:
چون هر دو سر تانل آی پی گرفته است آپ می شود
R3(config-if)#ip add 10.10.10.2 255.255.255.252
R3(config-if)#do ping 10.10.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/68/84 ms
R3(config-if)#exit
R3(config)#
R3(config)#
R3(config)#router eigrp 10
R3(config-router)#
R3(config-router)#no au
R3(config-router)#
R3(config-router)#network 10.10.10.2 0.0.0.0
R3(config-router)#network 172.16.2.1 0.0.0.0
*Nov 11 17:31:18.159:
R3(config-router)#
*Nov 11 17:36:38.395:
R3(config-router)#exit
R3(config)#
R3(config)#crypto isakmp enable
R3(config)#
R3(config)#crypto isakmp policy 10
R3(config-isakmp)#
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#
R3(config-isakmp)#hash sha
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#
R3(config-isakmp)#
R3(config-isakmp)#group 5
R3(config-isakmp)#
R3(config-isakmp)#
R3(config-isakmp)#
R3(config-isakmp)#exit
R3(config)#
R3(config)#crypto isakmp key 0 CBTNET add 192.168.1.1
R3(config)#
R3(config)#
R3(config)#crypto ipsec transform-set CR esp-3des esp-sha-hmac
R3(cfg-crypto-trans)#exit
R3(config)#
R3(config)#access-list 110 permit GRE any any
R3(config)#
R3(config)#crypto map MAP 10 ipsec-isakmp
and a valid access list have been configured.
آن را مشخص نکنیم غیر فعال است peerتازمانی که
R3(config-crypto-map)#
R3(config-crypto-map)#
R3(config-crypto-map)#set peer 192.168.1.1
R3(config-crypto-map)#set transform-set CR
R3(config-crypto-map)#
R3(config-crypto-map)#
R3(config-crypto-map)#match add 110
R3(config-crypto-map)#
R3(config-crypto-map)#
R3(config-crypto-map)#
R3(config-crypto-map)#exit
R3(config)#
R3(config)#
R3(config)#int s3/0
R3(config-if)#
R3(config-if)#crypto map MAP
R3(config-if)#
R3(config-if)#
R3(config-if)#
*Nov 11 17:41:26.863:
R3(config-if)#
*Nov 11 17:41:32.131:
R3(config-if)#
R3(config-if)#
R3(config-if)#exit
R3(config)#
R3(config)#^Z
R3#
*Nov 11 17:41:59.963:
R3#show crypto ipsec SA
interface: Serial3/0
Crypto map tag: MAP, local addr 192.168.2.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/47/0)
current_peer 192.168.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 11, #pkts encrypt: 11, #pkts digest: 11
#pkts decaps: 11, #pkts decrypt: 11, #pkts verify: 11
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 192.168.2.1, remote crypto endpt.: 192.168.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Serial3/0
current outbound spi: 0x1D5C89F7(492603895)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x1860ABCC(408988620)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000046, crypto map: MAP
sa timing: remaining key lifetime (k/sec): (4526244/3559)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x1D5C89F7(492603895)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000046, crypto map: MAP
sa timing: remaining key lifetime (k/sec): (4526244/3559)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R3#ping 172.16.1.1 source 172.16.2.1